SecureIT pre-session workshop

Thank you for attending the workshop!
We would appreciate it if you’d take the time to give us some feedback so we can continue to improve our events.
Post-Workshop Resources
- Contact OETC about the recommended cybersecurity toolset and presentation resources
- Eight actionable cybersecurity practices your institution should follow according to Jack Maynard
- How Salem-Keizer School District faces the rising tide of phishing attacks
- Learn how OETC members use KnowBe4 to prepare their staff to face cybersecurity threats.
Workshop Overview
| 8:30 a.m. |
Light Breakfast Served
|
| 9 a.m. |
Welcome and Introductions
|
| 9:15 a.m. |
Session 1: Ethically Hacking a School District – A Case Study
|
| 10:15 a.m. |
Break
|
| 10:35 a.m. |
Session 2: An Introduction to Open Source Intelligence (OSINT)
|
| 11:35 a.m. |
Debrief on Morning Sessions: Learnings & Observations
|
| 12 p.m. |
Working Lunch
Session 3: Tabletop Exercise – A Cyber Breach Has Occured. Now What? |
| 1 p.m. |
Debrief on Tabletop exercise: Learnings & Observations
|
| 1:20 p.m. |
Session 4: Developing a Cybersecurity Incident Response Plan (CSIRP)
|
| 1:50 p.m. |
Wrap-up and closing
|
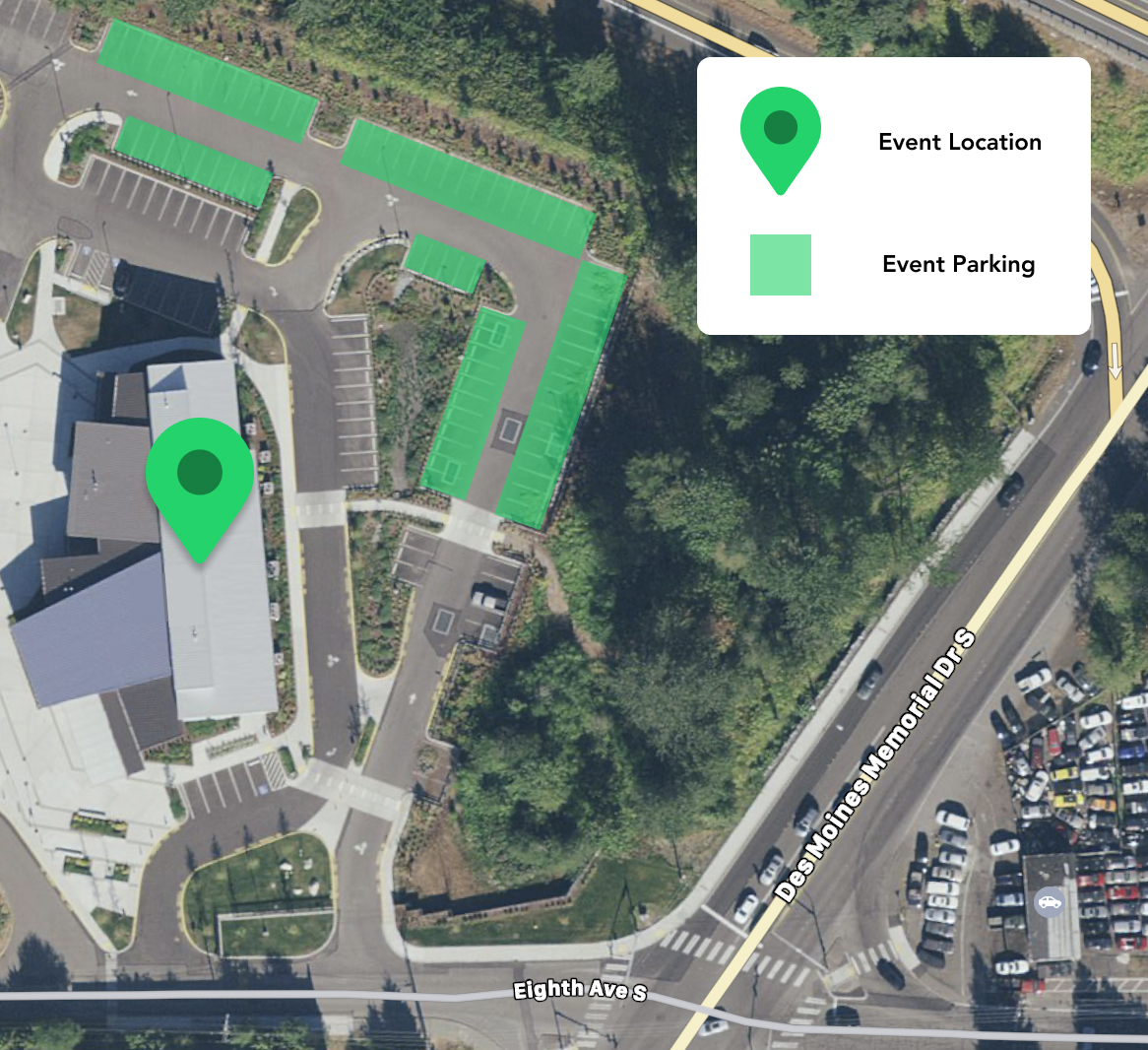
Location
Highline Public Schools
Puget Sound Skills Center
Lecture Hall
18010 8th Avenue South
Burien, WA 98148
Pre-Workshop Questions
Consider these questions, both generally and in the context of your district, to help you get the most out of the workshop:
Session 2: Introduction to Open Source Intelligence (OSINT)
- How do districts protect sensitive business information from exposure to criminal hackers while also serving the informationneeds of staff, parents and students?
- As taxpayer-funded entities, what information are districts legally required to share publicly? How might that be used by criminal hackers?
- What other sensitive information do districts typically overshare (not legally required to), but could be used against them by criminal hackers?
Session 3: A cyber-breach Has occurred. Now what?
In the event of a district cybersecurity incident or data breach:
- Who is in charge of the investigation?
- Who is part of the Incident Response team?
- What documents/evidence do you use to guide you in your investigation?
- What role does each district team — IT, HR, Legal, Finance, Communications —provide?
- Do you hire outside support?If so, who?
- What are you looking for? What would help you confirm a breach of your “crown jewels”?
Parking
Note: Please do not park in front of SeaMar clinic